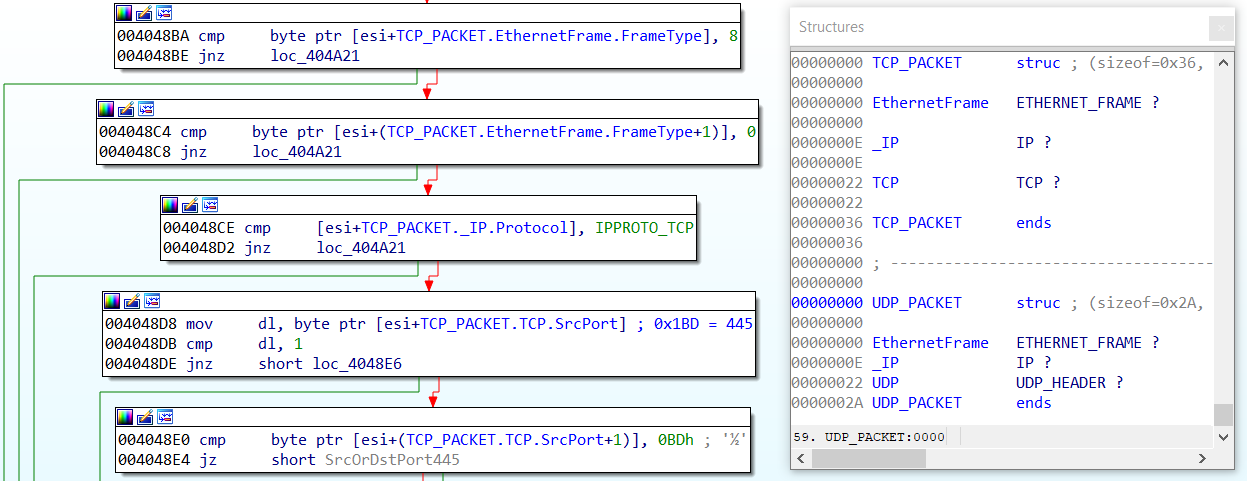
For many years I’ve been using custom Windows right-click menu entries to speed up common analysis tasks such as:
- calculate hash sums
- open a file in IDA Pro (
ida.exeorida64.exe) - zip a file (with password-protection “infected”)
- unzip a file (using password “infected”)
The result looks like this:
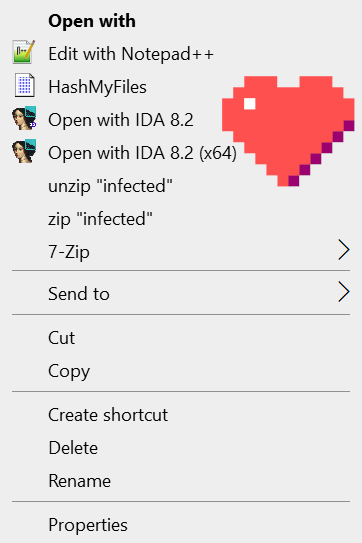
Recently, I set up a new analysis environment and very quickly missed these. So here they go for doing this more quickly in the future.
Continue reading “Windows Right-Click Menu Shortcuts: Open with IDA…”