I’ve recently analyzed a malware sample that parsed and modified raw network packet data. That means I had to deal with many register relative offsets in IDA Pro. The most practical way for this is to define and apply structs.
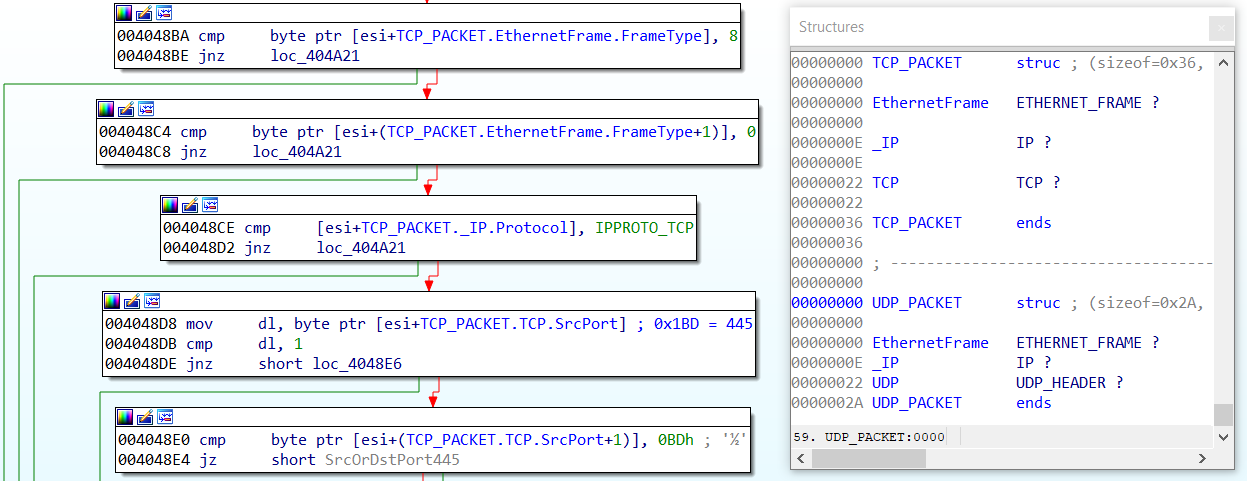
While IDA’s type libraries contain some of the packet structures (i.e., ETHERNET_FRAME, IP, TCP, and UDP_HEADER), other protocols (i.e., ARP) are missing. Additionally, I did not find structures encompassing multiple communication layers – for example ETHERNET_FRAME, IP, and TCP grouped in one structure.
Continue reading “IDA Pro structs for networking protocols: IP, TCP, UDP, ARP”