The FireEye Labs Obfuscated String Solver (FLOSS) automatically extracts obfuscated strings from Windows executables and shellcode. The tool integrates with various reverse engineering tools including IDA Pro, radare2, and x64dbg. In this post, I will show how to leverage strings that FLOSS decoded when reverse engineering malware using IDA Pro and debugging it using x64dbg.
For this analysis, I use a backdoor linked to APT28 and commonly referred to as Gamefish, Sednit, Seduploader, Jhuhugit, and Sofacy. The hash values of the file are:
- MD5:
211B7100FD799E9EAABEB13CFA446231 - SHA256:
3D13F2E5B241168005425B15410556BCF26D04078DA6B2EF42BC0C2BE7654BF8 - See https://virustotal.com/en/file/3d13f2e5b241168005425b15410556bcf26d04078da6b2ef42bc0c2be7654bf8/analysis/
I performed my analysis on a Windows 7 64-bit system setup with FLARE VM. If you haven’t heard about the project yet, you should really check out this malware analysis distribution at https://github.com/fireeye/flare-vm. Peter also describes the project in a blog post at https://www.fireeye.com/blog/threat-research/2017/07/flare-vm-the-windows-malware.html. FLARE VM already includes a wide variety of tools, including FLOSS and x64dbg.
FLOSS analysis
First, we run FLOSS on the sample to see the provided string deobfuscation results. As we are not interested in regular strings here, we disable showing them using the --no-static-strings command-line option. Listing 1 shows that FLOSS could deobfuscate 36 encoded strings and 14 stackstrings. The warning at the top of the output is related to vivisect’s vtrace module. It does not affect FLOSS’ analysis and can be ignored. Note, that updated FLOSS versions do no longer display the warning.
C:\Users\user\Desktop>floss --no-static-strings 211b7100fd799e9eaabeb13cfa446231.exe
WARNING:vtrace.platforms.win32:LoadLibrary c:\program files\python27\lib\site-packages\vtrace\platforms\windll\amd64\symsrv.dll: [Error 126] The specified module could not be found
WARNING:vtrace.platforms.win32:LoadLibrary c:\program files\python27\lib\site-packages\vtrace\platforms\windll\amd64\dbghelp.dll: [Error 126] The specified module could not be found
FLOSS decoded 36 strings
[file]
Execute
Delete
[/file]
www.google.com
192.111.146.185
192.111.146.185
w2f434g5Dt
.xml
rundll32.exe
FileName
PathToSave
Rundll
POST
Content-Type: application/x-www-form-urlencoded
0`AP
www.google.com
SYSTEM\CurrentControlSet\Services\Disk\Enum
POST
Content-Type: application/x-www-form-urlencoded
disk=
build=
POST
Content-Type: application/x-www-form-urlencoded
POST
Content-Type: application/x-www-form-urlencoded
CreateToolhelp32Snapshot
GetProcessHeap
GetProcessHeap
GetProcessHeap
GetProcessHeap
GetProcessHeap
GetProcessHeap
GetProcessHeap
GetProcessHeap
GetProcessHeap
FLOSS extracted 14 stackstrings
\profiles.ini
wininet.dll
InternetReadFile
network.proxy.http
Profile0
Basic
http=http://%s:%s
InternetCloseHandle
Path
network.proxy.http_port
WeelScrInit
Control Panel\Desktop
\Mozilla\Firefox
prefs.js
Finished execution after 15.682000 seconds
Listing 1: FLOSS analysis resultsx64dbg integration
Let’s pull the analysis results into x64dbg. We can create a x64dbg database file using the --x64db command-line option. This will create a JSON file containing the decoded strings and their offsets. Figure 1 shows a screenshot of running the following command:
C:\Users\user\Desktop>floss --no-static-strings --x64dbg=211b7100fd799e9eaabeb13cfa446231_floss.json 211b7100fd799e9eaabeb13cfa446231.exe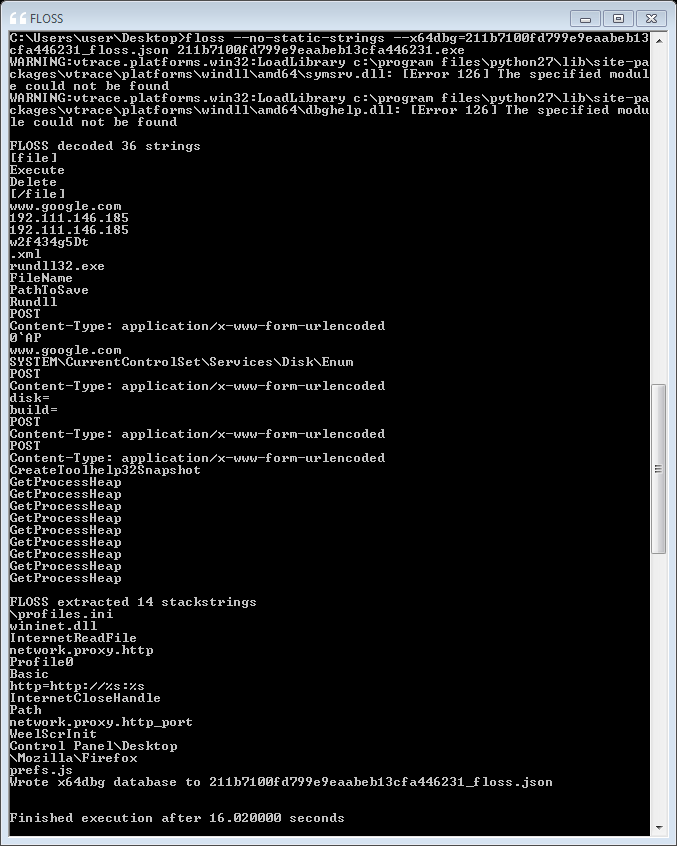
Now we can open the sample in x64dbg and load the FLOSS analysis results.
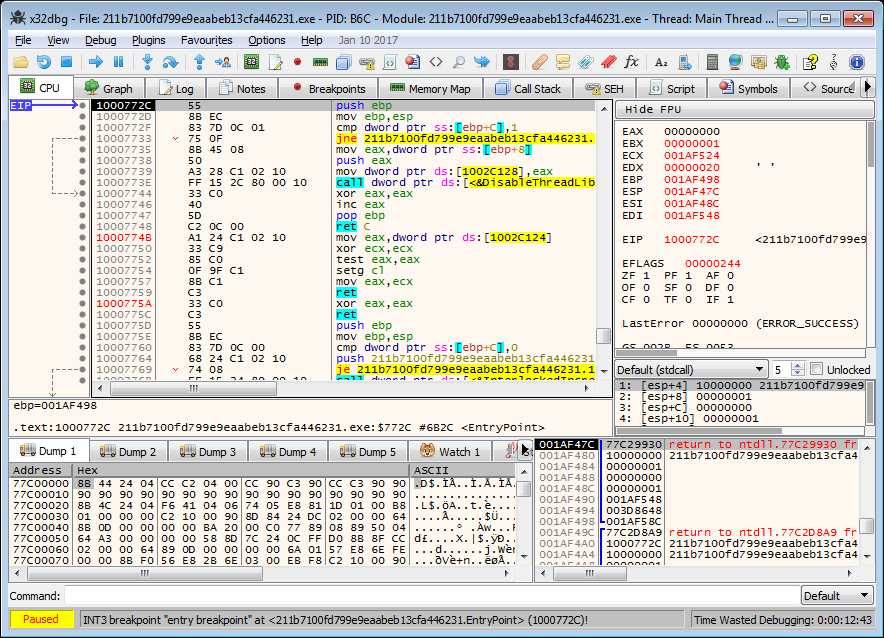
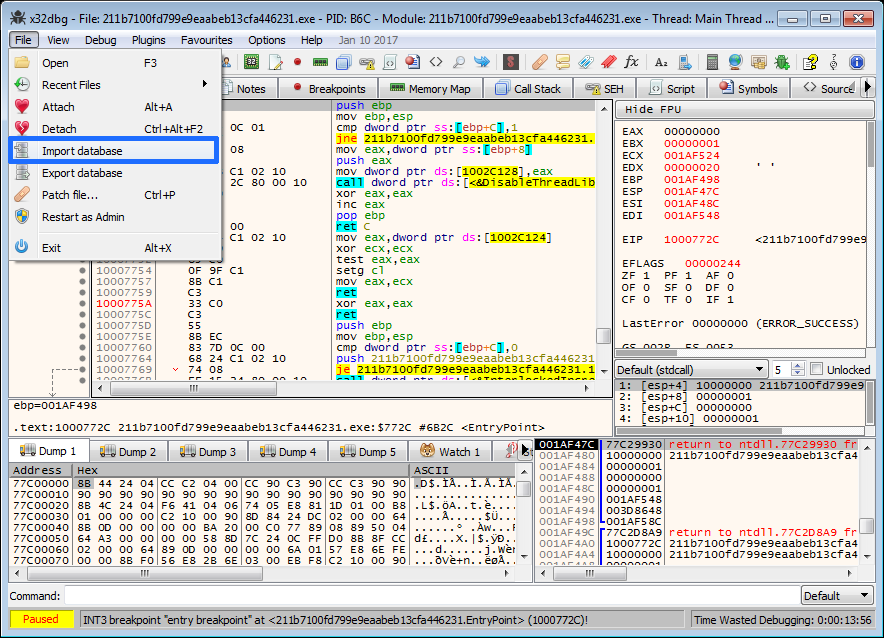
In x64dbg’s main menu use File – Import database to load the created database file (see Figure 3).
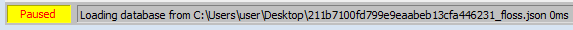
x64dbg will indicate that the file has been loaded in its status bar at the bottom of the window (see Figure 4).
In this example decoded strings are added as comments to the decoding function calls, e.g. the function at offset 0x10003FD4 (see Figure 5). If FLOSS detects obfuscated data at a global memory location, the decoded strings are added at the respective global offset. FLOSS does currently not support stackstring annotations for x64dbg.
IDA Pro integration
Provide the --i/--ida command-line option to FLOSS to create an IDAPython script that annotates IDA Pro’s disassembly. Here is an example command:
C:\Users\user\Desktop>floss --no-static-strings --ida=211b7100fd799e9eaabeb13cfa446231_floss.py 211b7100fd799e9eaabeb13cfa446231.exe
The tool indicates that the file has been written successfully:
[...] Wrote IDAPython script file to C:\Users\user\Desktop\211b7100fd799e9eaabeb13cfa446231_floss.py [...]
After opening the sample in IDA Pro, we can execute the created IDAPython script to annotate the disassembly. Select File – Script File (Shortcut Alt+F7) and load the script (see Figure 6).
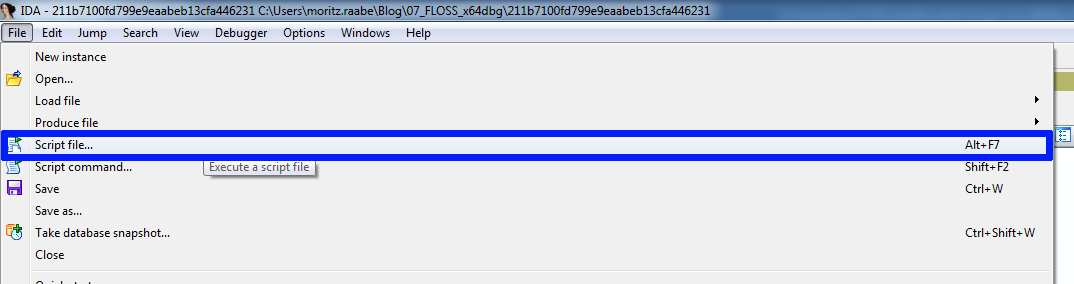
Figure 7 shows the script’s execution status information displayed in IDA Pro’s output window.
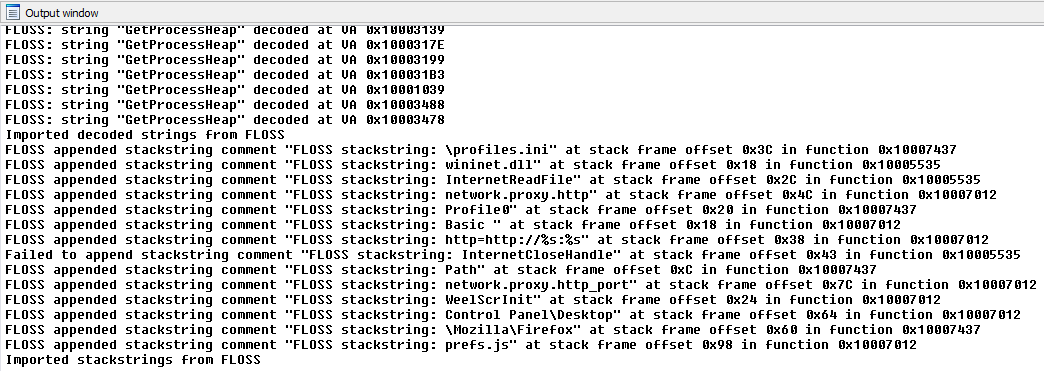
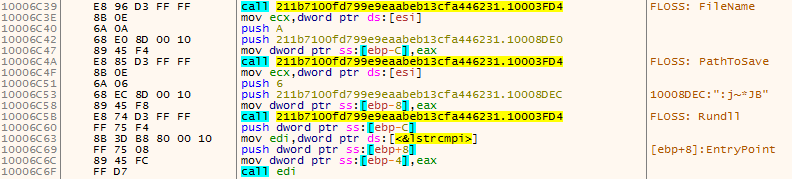
Figure 8 shows calls to the decoding routine at offset 0x10003FD4 that have been annotated with the decoded strings.
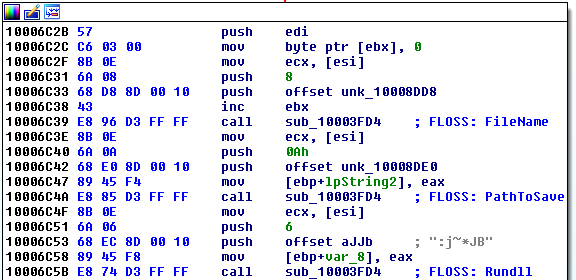
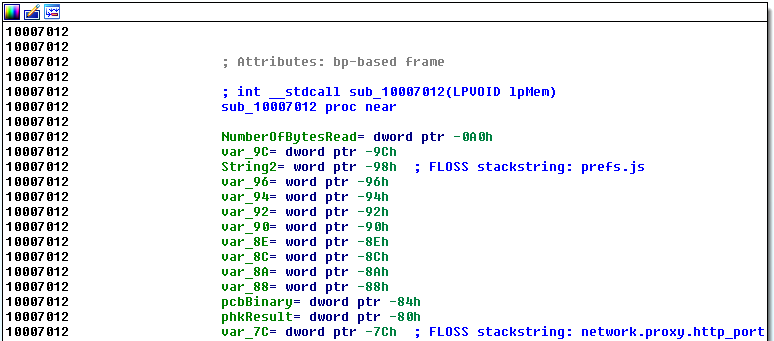
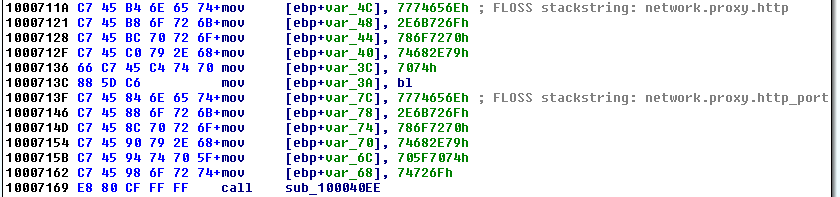
Figure 9 shows the FLOSS annotations from deobfuscated stackstrings. Each decoded stackstring is added as repeatable comment to the respective local variable. Hence, IDA Pro displays them whenever the local variable is referenced (see Figure 10).
Conclusion
This post discussed how the analysis of FLOSS can augment the analysis of malware in IDA Pro and x64dbg. Hopefully, I could show the benefit of pulling FLOSS results into both tools. While the process is straight-forward in either case, I am sure this step-by-step tutorial can be helpful – especially when you are doing it for the first time.